I was recently engaged with a large health-care provider in deploying a set of FortiWeb VMs to protect a number of web applications. Part of this deployment included setting up Single-Sign on for the admin interface using Microsoft Entra ID (Azure AD). While the process is fairly straightforward it is a little confusing at some points, so I’ve wrote this just in case you or I need this again.
I was recently engaged with a large health-care provider in deploying a set of FortiWeb VMs to protect a number of web applications. Part of this deployment included setting up Single-Sign on for the admin interface using Microsoft Entra ID (Azure AD). While the process is fairly straightforward it is a little confusing at some points, so I’ve wrote this just in case you or I need this again.
Start off by creating an Enterprise Application in Microsoft Entra, browse the gallery and use the pre-built FortiWeb Web Application Firewall (which is used client based web authentication) – instead we’ll use it to configure the admin login. Enable Single sign-on and enter the Basic SAML configuration details as follows:
Identifier (Entity ID): http://10.0.0.1/metadata
Reply URL (Assertion Consumer Service URL): https://10.0.0.1:4443/saml/?acs
Sign on URL: https://10.0.0.1:4443/saml/login
The important part here is that the identifier runs on http and without the admin port, where as your reply and sign on URLs will need to go via https to the admin port. Copy the Login URL (the logout URL is almost always the same…) and Microsoft Entra Identifier as we’ll need these shortly. Add yourself or test user we’ll be logging in with. We can now move onto configuring the FortiWeb.
Login and navigate to Security Fabric > Fabric Connectors and click on the FortiGate and select edit. Once in, we’ll enable Single Sign-On mode toggle and enter some details as follows:
SP Address: IP of FortiWeb (primary if HA)
Default Login Page: Leave as Normal
Default SSO Admin Profile: admin_no_access
IDP Entity ID: paste the Entra Identifier here
IDP Single Sign-On URL: paste the Login URL here
IDP Signle Logout URL: paste the Login url here
Unlike a FortiGate we don’t need to specify or upload an IDP certificate. Also for Default SSO admin profile this means you’ll need to create the user and manually set the profile – otherwise any user who logs in will get this profile such as prof_admin automatically. Once done you should have something similar to the image. Click OK to save the configuration.
Now, hopefully you’ve set it to admin_no_access – so let’s create a user by going to System > Admin > Administrators, under Create New, click SSO Admin. For the username enter the user principal name of the Entra user and click OK.
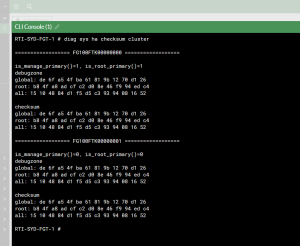
 You should now be ready to test the SAML sign in. Fire up an incognito browser and once you hit the login page, you should see the text or via Single Sign-On next to the Login button. If you get an error on the FortiWeb side or sent back to the login page, you can do some additional debugging to check Assertions and the like via the console by using the following debug commands (excuse my shorthand of diagnose debug)
You should now be ready to test the SAML sign in. Fire up an incognito browser and once you hit the login page, you should see the text or via Single Sign-On next to the Login button. If you get an error on the FortiWeb side or sent back to the login page, you can do some additional debugging to check Assertions and the like via the console by using the following debug commands (excuse my shorthand of diagnose debug)
# di de app samld 7
# di de en
Once you are done inspecting, make sure to disable diagnose mode
# di de di
Enjoy.
Share this post with others:
 We recently had a customer take advantage of a free upgrade from FTTN (Fibre to the Node) to FTTP (Fibre to the Premise) for their NBN (National Broadband Network) service. However during cut-over the FortiGate wasn’t picking up connectivity on the WAN port, this had the on-site guy stumped for 10 minutes until we jumped on and took a look. In HFC days, you’d sometimes have to “spoof” the MAC address to get it working – but in this case it was something else… Ethernet auto-negotiate.
We recently had a customer take advantage of a free upgrade from FTTN (Fibre to the Node) to FTTP (Fibre to the Premise) for their NBN (National Broadband Network) service. However during cut-over the FortiGate wasn’t picking up connectivity on the WAN port, this had the on-site guy stumped for 10 minutes until we jumped on and took a look. In HFC days, you’d sometimes have to “spoof” the MAC address to get it working – but in this case it was something else… Ethernet auto-negotiate.