So getting BitLocker enabled in an Active Directory environment is fairly painless and helps to get your end user devices more Secure. I’ll outline the steps you need to take to enable it as well as get the recovery keys stored in Active Directory. I’ll also dive into replicating this setup on Azure AD/Intune in a future post.
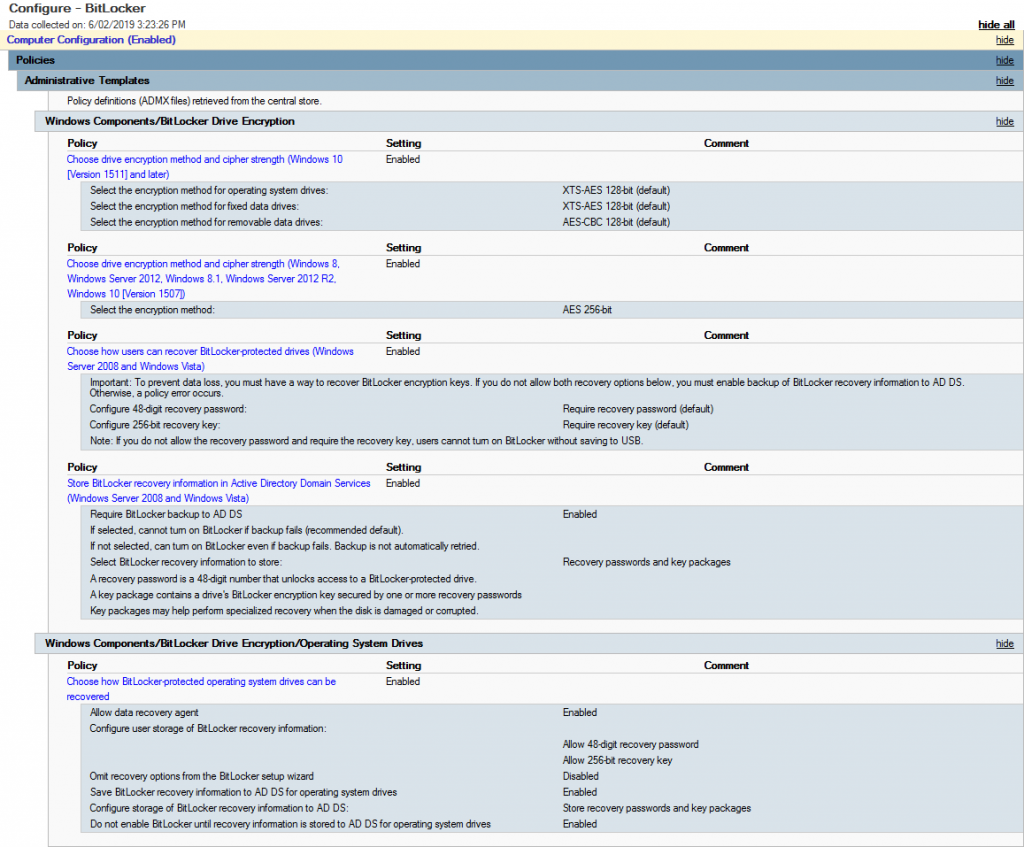
First thing is to create a new GPO (i.e. Configure – BitLocker) – Edit it and navigate to Policies > Administrative Templates > Windows Components > BitLocker Drive Encryption. Enable the following Options:
- Choose drive encryption method and cipher strength (Windows 10 Version 1511 and later)
- Choose drive encryption method and cipher strength (Server 2012, Win 8.1 etc…)
- Choose how users can recover BitLocker protected drives
- Store BitLocker recovery information in Active Directory Domain Services
Then go down one folder into Operating System Drives and enable the following:
- Choose how BitLocker protected operationg system drives can be recovered
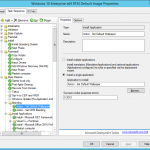
Once you’ve set this all up, it should look something similar to the image below.
Now target the GPO to some machines and if you’re running 1809 (from what I’ve discovered so far) or later you’ll notice them start the BitLocker process to encrypt automatically. If not then you may need to check and ensure the TPM is enabled for the device (as we haven’t specified to encrypt devices without a TPM in this case).
What happens if you have already enabled BitLocker but now want to store the recovery keys in Active Directory? With this GPO set it will allow windows to write the recovery key to AD however we need to use the manage-bde utility, that is a command based utility that can be used to configure BitLocker
manage-bde -protectors -get c:
for /f "skip=4 tokens=2 delims=:" %%g in ('"manage-bde -protectors -get c:"') do set MyKey=%%g
echo %MyKey%
manage-bde -protectors -adbackup c: -id%MyKey%
I saved that as a batch file and ran that on the machines that had already been encrypted prior to rolling out the GPO. Once run, it escrows the key into Active Directory.
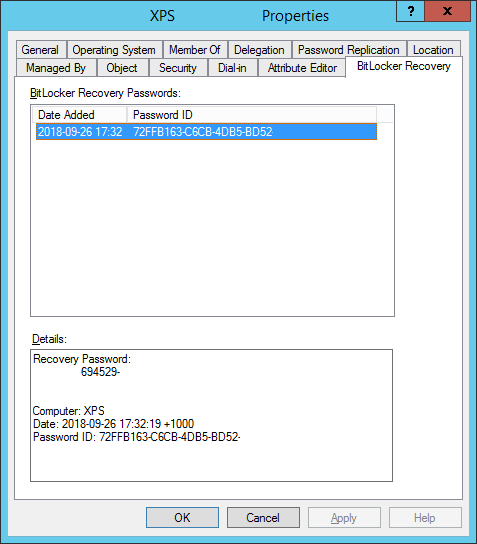
The last bit you will need to do so you can actually see the keys in the Properties tab or via the Search function in Active Directory Users and Computers, ensure that the BitLocker RSAT is enabled in Server Features and Roles.