Long time since I’ve posted – I promise I’ve been very busy with life.
Long time since I’ve posted – I promise I’ve been very busy with life.
I was recently assisting a customer with a CrowdStrike Falcon Sensor deployment and we were in the process of updating the gold images in their VDI platform, Amazon WorkSpaces. CrowdStrike have a nice installation document on their website that you can follow to get the sensor deployed. After going through the process (starting from about page 10 since we already have WorkSpaces and using the yearly billing option), we deployed the sensor with the following parameters, with the NO_START being important so that the sensor doesn’t imprint IDs (similar to most other cloud managed tooling).
WindowsSensor.exe /install /norestart CID=<falcon id here> NoFA=1 NoDC=1 NO_START=1
After executing and the progress bar getting about half way, we ended up encountering an error. CSFalconServiceUninstallTool_x64.exe – Bad Image relating to spacedeskHookUmode.dll Reading up in the CrowdStrike support portal, the error usually relates to Citrix or some sort of DLP protection triggering, however we had neither operating in the VDI environment.
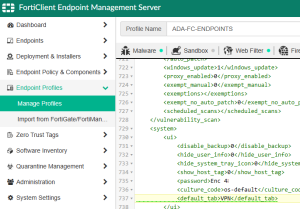
After some further digging, we found a PDF on the Amazon site and found that the culprit is actually part of Amazon WorkSpaces, as the dll file provides the ability to use Web Access. In our use case, we don’t use this so simply set the following registry keys to disable web access in the image.
HKEY_LOCAL_MACHINE\SOFTWARE\Amazon\WorkSpacesConfig\update-webaccess.ps1
Set the RebootCount DWORD to 1
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\spacedeskHookKmode
Set the Start DWRORD to 4
Once done, we rebooted and then had a successful sensor install.
Hope that helps.